
The procedure during a penetration test is defined differently on many sites. In this article we want to go into the differences between "on-site" pen tests and "remote" pen tests.
An Penetration test is no longer what was understood as black box testing in the 90s. Nowadays, a lot more is needed to be able to establish a certain security standard. In the context of information security, the human factor and physical security must also be taken into account. In the following, we will show you whether a remote pentest or an on-premise pentest is more suitable for your purposes and what is actually done during a pentest.
Average penetration tests can be divided into three stages in terms of procedure.
First comes what most people think of as "Chopknow and hear. You look at the external events of a target and try to get as much information as possible in order to then find suitable vectors of incidence. Classic examples would be the CMS (Content Management System) of the website such as WordPress or Typo3, certain functionalities such as customer/supplier portals or online shops, but also general services that are public to the outside (Outlook, Mail, etc.) .
In the best-case scenario (on the part of the customer), there are no direct, serious ways of getting into the internal network from the outside. Therefore, the human factor is used as an alternative, since this is still the simplest goal in every company. About a targeted Social Engineering Scenario one gets into the internal network of the customer and from there the bulk of an on premise or remote pentest begins.
If the hacker has made it into a customer's internal network, the question naturally arises as to what damage he can cause there. To answer this question, an insider or infected device is simulated. There are two ways to do this: You place the pen tester on site in the company and have it tested over the period of time or you can carry out a remote pentest using a jump host.
We from per sec have found a self-developed solution for on-premise and remote pentests: our Pentest Box. It serves as an extended arm of the pentester and simulates an infected client or internal perpetrator in the customer's network, both in the on-premise and in the remote pentest.
Such an intrusion occurs through phishing or possibly through a disgruntled employee who wants to cause damage. The only difference between our pentest box and an infected client is that we are not an active user in Active Directory, which is not a major hurdle.

In addition, the admin does not have to worry about leaving a client with hacker tools in the network or having to bother to set up the client again. Our pentest box makes both on premise and remote pentests easier and allows us to ensure the best protection for your business.
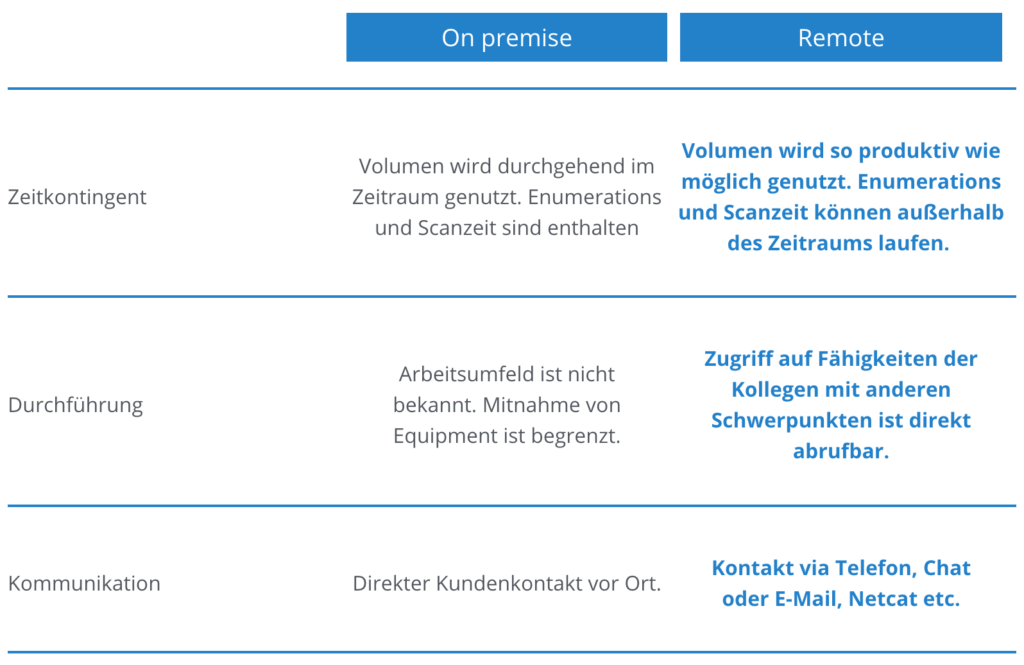
time quota
Volume is used throughout the period. Enumerations and scan time are included
Volume is used as productively as possible. Enumerations and scan time can run outside of the period.
Execution
Working environment is unknown. Equipment is limited.
Access to the skills of colleagues with other areas of focus can be called up directly.
Communication
Direct customer contact on site.
Contact via phone, chat
or Email, Netcat etc.
Would you like to learn more about remote pentesting? Here for contact
In contrast to remote pentests, "on premise" tests can quickly become expensive. Since a penetration test takes several weeks on average, the penetration tester needs accommodation, travel costs + expenses over this period.
One advantage, of course, is that the pentester is “physically” on site, which means that there is much more knowledge transfer than just a “video conference” in the course of a remote pentest. In order to strive for knowledge transfer here, ProSec offers a clear basis for the topics via the results, the final presentation and the action plan.
Of course, the advantages of a remote pentest outweigh the disadvantages, e.g. that the continuous power supply to the pentest box MUST be guaranteed. The connection can also be broken or blocked by the firewall, so the box must also be "whitelisted" in individual cases. However, these problems can easily be circumvented in the course of a remote pentest through two-way communication between the single point of contact.
Since penetration tests are always tailored to the protection needs of each company, it makes sense to consider the economic and time resources, as well as the degree of realism of an attack. It is therefore advisable to use a "remote" pentest as a rule.
The "on premise" variant makes sense if a company's focus is on security requirements and knowledge transfer is a priority.

