
To compromise enterprise and cloud environments.
Network admins should adopt and expand the use of multi-factor authentication to mitigate the effectiveness of these attacks. Additional access control measures include time-out and lock-out features, use of strong passwords, implementation of a Zero Trust security model that uses additional attributes to determine access, and analytics to detect anomalous access. Additionally, organizations may consider denying all inbound activity from well-known anonymization services such as commercial Virtual Private Networks (VPNs) and The Onion Router (TOR) when such access is not associated with typical usage.

The attackers used a combination of known TTPs in addition to their password spray operations to exploit target networks, access additional credentials to penetrate deeper, and collect, orchestrate, and exfiltrate data, as shown in the image below. The attackers used a variety of protocols, including HTTP(S), IMAP(S), POP3, and NTLM. The attackers also used various combinations of TTPs to bypass defenses and to obfuscate some components of their operations; however, many detection avenues remain to identify the activities.
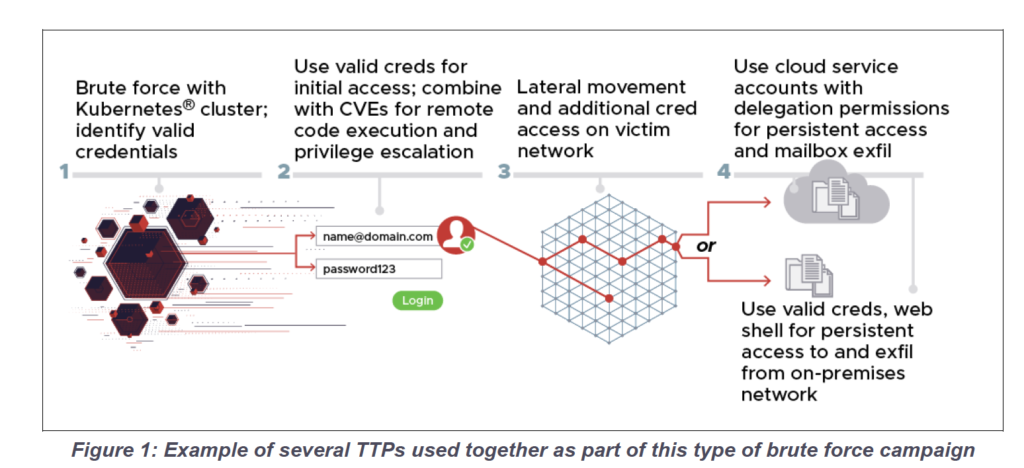
The table below summarizes the known TTPs used in conjunction with the password spray feature. Because the structure of target networks can vary widely, the 85th GTsSS may use a subset of these TTPs, or other TTPs not included in this summary, against different victims.
Table I: Summary of known tactics, techniques and procedures
| Taktik | Technology | Procedures/Comments |
| Initial access | T1190 1 - Use of Public Facing Applications | The attackers used a number of public exploits, including CVE 2020-0688 and CVE 2020-17144, to gain privileged remote code execution on vulnerable Microsoft Exchange servers. In some cases, this exploit occurred after valid credentials were identified by Password Spray, as these vulnerabilities require authentication as a valid user. |
| Initial Access, Persistence and Privilege Escalation | T1078—Valid Accounts | The attackers used legitimate credentials obtained through various means to gain access to the targeted networks. |
| P | T1078.002 - Valid Accounts: Cloud Accounts | The attackers used a compromised Office 365 service account with global administrator rights to harvest emails from users' inboxes. |
| P | T1505.003—Web shell | The attackers used a modified and obfuscated version of the reGeorg web shell to gain persistent access to a target's Outlook Web Access (OWA®) server. |
| P | T1098.002 – Account Manipulation: Exchange Email Delegate Permissions | The attackers used a Powershell® cmdlet (New-ManagementRoleAssignment) to grant the ApplicationImpersonation role to a compromised account. |
| CredentialAccess | T1110.003 - Password Spray | The attackers run a Kubernetes cluster that allows them to perform distributed and large-scale attacks using password spray and password guessing. |
| CredentialAccess | T1003.001 - LSASS Memory | The attackers dumped the LSASS process memory by using rundll32.exe to run the MiniDump function, which is exported by the native Windows® DLL comsvcs.dll. |
| CredentialAccess | T1003.003 – NTDS | The attackers used the ntdsutil.exe utility present on a target's Active Directory® server to export the Active Directory database for credential access. |
| Remote services | T1021.002 - SMB/Windows Admin Shares | The attackers mapped network drives using “net use” and administrator credentials. |
| Collection | T1560.001 – Archive Collected Data: Archive via Utility | The attackers used a variety of utilities, including publicly available versions of WinRAR®, to archive the collected data with password protection. |
| Collection | T1005—Data from Local System | The attackers collected files from local systems. |
| Collection | T1039 - Data from Network Shared Drive | The attackers collected files located on a shared network drive. |
| Collection | T1213 - Data from Information Repositories | The attackers collected files from various information depots. |
| Collection | T1074.002—Remote Data Staging | The attackers deployed archives of the collected data on a target's OWA server. |
| Collection | T1114.002—Remote Email Collection | The attackers harvested emails from Office 365 using a compromised valid service account with elevated privileges. |
| Command and control | T1115 - Ingress Tool Transfer | The attackers used certutil.exe, a well-known “living off the land” technique, to transfer a file to a target environment. |
| Defense Evasion | T1036 - Masquerading | The attackers renamed archive files containing exfiltration data with harmless-looking names and extensions (e.g. .wav and .mp4) to resemble benign files. |
| P | T1098.002 – Account Manipulation: Exchange Email Delegate Permissions | The attackers used a Powershell® cmdlet (New-ManagementRoleAssignment) to grant the ApplicationImpersonation role to a compromised account. |
| CredentialAccess | T1110.003 - Password Spray | The attackers run a Kubernetes cluster that allows them to perform distributed and large-scale attacks using password spray and password guessing. |
| CredentialAccess | T1003.001 - LSASS Memory | The attackers dumped the LSASS process memory by using rundll32.exe to run the MiniDump function, which is exported by the native Windows® DLL comsvcs.dll. |
| CredentialAccess | T1003.003 – NTDS | The attackers used the ntdsutil.exe utility present on a target's Active Directory® server to export the Active Directory database for credential access. |
| Remote services | T1021.002 - SMB/Windows Admin Shares | The attackers mapped network drives using “net use” and administrator credentials. |
| Collection | T1560.001 – Archive Collected Data: Archive via Utility | The attackers used a variety of utilities, including publicly available versions of WinRAR®, to archive the collected data with password protection. |
| Collection | T1005—Data from Local System | The attackers collected files from local systems. |
| Collection | T1039 - Data from Network Shared Drive | The attackers collected files located on a shared network drive. |
| Collection | T1213 - Data from Information Repositories | The attackers collected files from various information depots. |
| Collection | T1074.002—Remote Data Staging | The attackers deployed archives of the collected data on a target's OWA server. |
| Collection | T1114.002—Remote Email Collection | The attackers harvested emails from Office 365 using a compromised valid service account with elevated privileges. |
| Command and control | T1115 - Ingress Tool Transfer | The attackers used certutil.exe, a well-known “living off the land” technique, to transfer a file to a target environment. |
| Defense Evasion | T1036 - Masquerading | The attackers renamed archive files containing exfiltration data with harmless-looking names and extensions (e.g. .wav and .mp4) to resemble benign files. |
| Defense Evasion | T1036.005—Match Legitimate Name or Location | The attackers named an instance of their web shell “outlookconfiguration.aspx,” likely to make it appear that it was a legitimate website on a targeted OWA server. |
| exfiltration | T1048.002 - Exfiltration Over Asymmetric Encrypted Non-C2 Protocol | The attackers downloaded archives containing collected data previously served on a target's OWA server over HTTPS. |
| exfiltration | T1030—Data Transfer Size Limits | The attackers split some archived exfiltration files into chunks smaller than 1MB. |
To disguise its true origins and maintain a level of anonymity, the Kubernetes cluster typically routes brute-force authentication attempts through TOR and commercial VPN services, including CactusVPN, IPVanish®, NordVPN®, ProtonVPN®, Surfshark®, and WorldVPN. Authentication attempts that did not use TOR or a VPN service were also sometimes delivered directly to the targets from nodes in the Kubernetes cluster.
The scalable nature of the password spray capability means that certain indicators of compromise (IOC) can be easily modified to bypass IOC-based mitigation. In addition to blocking activity related to the specific indicators listed in this Cybersecurity Advisory, organizations should consider denying all inbound activity from known TOR nodes and other public VPN services to Exchange servers or portals where such access is unrelated to typical usage.
• 158.58.173[.]40 • 185.141.63[.]47 • 185.233.185[.]21 • 188.214.30[.]76 • 195.154.250[.]89 | • 93.115.28[.]161 • 95.141.36[.]180 • 77.83.247[.]81 • 192.145.125[.]42 • 193.29.187[.]60 |
In cases where HTTP was the underlying protocol used to transmit authentication requests, the attackers used many different user-agent strings designed to match those sent by legitimate client software . Some of the user-agent strings submitted in the authentication requests are incomplete or truncated versions of legitimate user-agent strings and offer the following unique detection capabilities:
• 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70'.
• 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36'
• 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:63.0) Gecko/20100101 Firefox/63.0'
• 'Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36'
• 'Mozilla/5.0 (Macintosh; Intel Mac OS
• 'Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7162; Pro'
• 'Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7166; Pro)'
• 'Microsoft Office/14.0 (Windows NT 6.1; Microsoft Outlook 14.0.7143; Pro)'
• 'Microsoft Office/15.0 (Windows NT 6.1; Microsoft Outlook 15.0.4605; Pro)'
The following Yara rule matches the reGeorg variant web shell used by the attackers. Because this is a publicly-facing web shell, the rule does not uniquely identify malicious activity by the 85th GTsSS.
rule reGeorg_Variant_Web shell {
strings:
$pageLanguage = "<%@ Page Language=\"C#\""
$obfuscationFunction = "StrTr"
$target = "target_str"
$IPcomms = "System.Net.IPEndPoint"
$addHeader = "Response.AddHeader"
$socket = "Socket"
condition:
5 of them
}
As with other credential theft techniques, organizations can take the following actions to ensure strong access control:
1] Norwegian Police Security Service (PST), “Datainnbruddet mot Stortinget er ferdig etterforsket,” December 8, 2020. https://www.pst.no/alle-artikler/pressemeldinger/datai nnbruddet-mot-stortinget-er-ferdig -etterforsket/
[2] Microsoft Threat Intelligence Center (MSTIC), “STRONTIUM: Detecting new patterns in credential harvesting.” September 10, 2020. https://www.microsoft.com/ security/ blog/2020/09/10/strontium-detecting-new-patters-credential-harvesting/
[3] National Security Agency, “Detect and Prevent Web Shell Malware.” April 22, 2020. https://www.nsa.gov/cybersecurity-guidance
[4] National Security Agency, “Selecting Secure Multi-factor Authentication Solutions.” October 16, 2020. https://www.nsa.gov/cybersecurity-guidance
[5] National Security Agency, “Mitigating Cloud Vulnerabilities.” January 22, 2020. https://www.nsa.gov/cybersecurity-guidance
[6] National Security Agency, “Embracing a Zero Trust Security Model.” February 25, 2021. https://www.nsa.gov/cybersecurity-guidance
The information and opinions contained in this document are provided “as is” and without any representation or warranty of any kind. Reference to any particular commercial product, process, or service by trade name, trademark, manufacturer, or otherwise does not constitute endorsement, recommendation, or favoring by the United States Government, and this guide may not be used for advertising or product endorsement purposes.
Active Directory, Microsoft Exchange, Office 365, Office, Outlook, OWA, Powershell, Windows and Windows NT® are registered trademarks of Microsoft Corporation. – Kubernetes is a registered trademark of the Linux Foundation. – WinRAR is a registered trademark of Roshal, Alexander. - IPVanish is a registered trademark of Mudhook Marketing, Inc. - NordVPN is a registered trademark of NORDSEC PLC. – ProtonVPN is a registered trademark of Proton Technologies AG. – Surfshark is a registered trademark of SURFSHARK LTD. – Firefox® and Mozilla® and are registered trademarks of the Mozilla Foundation. – Chrome® is a registered trademark of Google, Inc. – Mac® and WebKit® are registered trademarks of Apple, Inc.
This document was developed by the NSA, CISA, FBI, and NCSC to advance their respective cybersecurity missions, including their responsibilities for developing and issuing cybersecurity specifications and remediation actions. This information can be shared widely to reach all appropriate stakeholders.
Customer Requirements / General Cybersecurity Inquiries: Cybersecurity Requirements Center, 410-854-4200, Cybersecurity_Requests@nsa.gov
Media Inquiries / Press Desk: 443-634-0721, MediaRelations@nsa.gov