
An IT security audit refers to a security and risk analysis based on existing weak points and security gaps, processes or organizational measures in a company.
Security gaps can affect both computer systems and computer programs used in the respective companies. Vulnerabilities or security gaps are largely based on errors in design and implementation. They also include design and construction errors as well as human error (algorithms) in a programmed application (computer program/service).
The identification and exploitation of these vulnerabilities by criminals can cause financial risks and economic damage to the company. IT vulnerability analyzes aim to systematically find these errors in order to prevent or minimize threats and possible attack scenarios before these issues are discovered and exploited by criminals.
In most cases, the IT security audit begins as part of quality management in order to identify and evaluate the problems mentioned. It is important to implement comprehensive quality management, for example after software has been developed, in order to prevent the most common errors and to ensure basic security of the environment and the software that will later be operated in companies.
This also includes external dependencies, such as the IT infrastructure and IT environment (operating system) on which the application is operated, in order to analyze, evaluate and evaluate potential impacts. These are also part of a risk and vulnerability analysis. IT security audits also belong to the area of information and network security, which is absolutely necessary in this context.
Technical weaknesses or missing measures are often the result of an incomplete IT security concept. In some cases there is no documented IT security concept from which the technical measures can be derived.
Does the company have a uniform understanding of which information is more worthy of protection than others and on which systems it is processed?
Are there clear guidelines on how different information should be handled?
For example, marketing catalogs can probably be disposed of as “simple” paper waste, while special shredders with particularly small cutting sizes may be intended for personnel documents and business figures. Such different processes and procedures must be recorded in the form of organizational instructions to ensure a uniform level of security.
As part of an IT security audit, it is therefore important not only to look at the technical weak points, but also to examine the organizational framework.
Internationally, IT security audits are becoming the norm ISO / IEC 27001 of ISO set. This usually includes international security policies that are related to planning, documentation and constant development of the company's information security management system (ISMS). Further national standards are based on the BSI IT security manual with the following distinctions using a diagram:
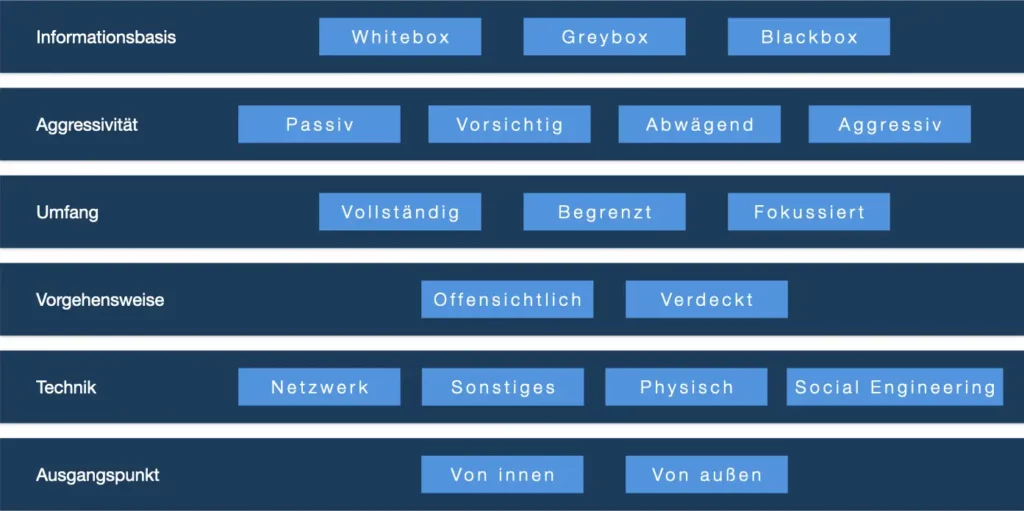
Results and evaluations of IT security audits are based on a so-called catalog of measures (action plan), which forms the basis for further steps to eliminate security gaps and vulnerabilities by IT or administrators of the company's internal IT department. The catalog of measures also shows the exact impact on the company, a solution approach for remediation and additional data protection-relevant topics, i.e. whether a security gap can also affect data protection.
Based on this, IT has an overview of the actual and target state of the situation and can use this to estimate, after a risk analysis, to what extent the company needs IT security or not. Based on the results of the catalog of measures, employees can be retrained or further trained using certificates in order to ensure a better IT environment within the area of application in the future.
