
In one of our last posts, we showed how we LLMNO (Link-local Multicast Name Resolution) poisoning obtained information and password hashes through a man-in-the-middle attack. In this article we would like to take care of the "predecessor protocol" NBT-NS (Netbios Nameservice), with which we can also "poison" the packets.
NetBios over TCP/IP or NBT-NS is an old protocol for name resolution if the DNS servers in the network cannot provide suitable names. The host uses this protocol as a broadcast to search for the appropriate service itself.
Netbios is used in Windows versions up to Windows ME to implement higher network functions (Server Message Block (SMB)). Newer Windows versions from Windows 2000 handle the SMB communication directly via TCP port 445.
By default, NetBIOS over TCP/IP support is enabled for all interfaces in all versions of Windows.
The log is on the following ports:
UDP 137: Name resolution
UDP 138: Datagram Service
TCP 139: Session service
The way the protocol works can be set across five nodes.
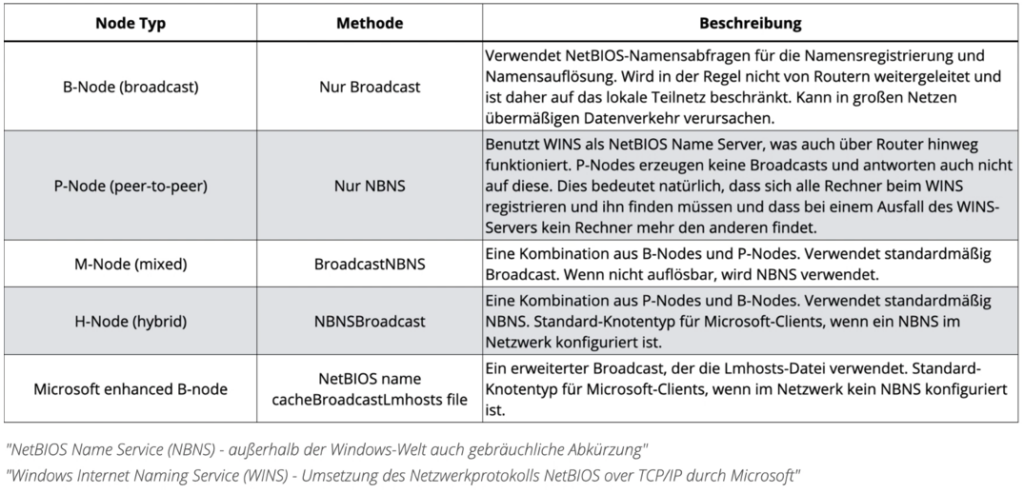
By default, NBT-NS uses the H-Node (hybrid) for name resolution and name registration. This is a combination of broadcast requests (B-Node) and peer-to-peer requests (P-Node).
Similar to an LLMNR poisoning attack, NTB-NS is used without a suitable response from the DNS server.
This means that an attempt is made to find an answer in the local network. This usually happens when the user makes a typo when searching for a network resource, is not in the right network, has not configured a DNS server or, for example, has forgotten what to do with it VPN to connect and therefore cannot reach the desired network resource.
In this case, the attacker can send the client a reply that he knows the network resource and send him the IP of the desired resource. He should be able to reach the network resource via this IP. However, this IP arrives at the server hosted by the attacker.
The client now sends a request to the IP address given to it. However, so that the supposed authorization of the client can be checked, the attacker demands authentication from the client. This can take place via Basic-Auth or Challenge-Response (such as Net-NTLMv2). After authentication, the client gets an error message that makes it look like the resource wasn't found after all. In most cases, authentication takes place without user interaction.

The tool can be used to technically implement the NBT-NS Poisoning attack just explained Reply should be used.
The following command can be used to start Responder:
responder -I
In the example photo, a client authenticated itself with Net-NTLMv2 in response to the attacker's response.
Responder offers a variety of settings and servers and can also be configured for targeted attacks.
There are various options to prevent NBT-NS attacks or to deactivate NBT-NS use. From setting via DHCP to deactivation via GPO.
An extended option can be given for all interfaces in the DHCP server options: 001 Microsoft NetBIOS disable option - 0x2
When a system receives a DHCP lease, NetBIOS is automatically disabled on all interfaces.
The node type can also be specified via registration and GPO. This change changes the NodeType to P (Peer-to-Peer). So there is no name resolution via NBT-NS.

Under the network options, select TCP/IPv4, Advanced, WINS - the option "Disable Netbios over TCP/IP" can be selected.
This customization can also be rolled out using a Powershell script via a GPO in the domain.

After disabling NBT-NS in your network, it is worth analyzing the network traffic. In the course of this, you can also see whether there were problems with the implementation of the hardening measures, or whether new systems may not have been configured according to this new standard. If you pay attention to this, you have optimally closed an attack vector permanently.
Search for Broadcast NBT-NS Traffic or configure an IDS rule (example here for Snort).
alert udp any 137 -> any 137 (msg:"NetBIOS NBT\-NS Query Broadcast"; content:"|01 10|"; depth: 46; reference:url,prosec-networks.com/blog/netbios-tcp; classtype:non-standard-protocol; sid:1000001; rev:001;)
In order to detect an attacker in the network, there are tools that send targeted NBT-NS requests for non-existent resources into the network. If you now get answers to these requests, there is an attacker in the network waiting for NBT-NS requests.
To actively detect an attacker in the network, tools such as: Conveigh or HoneyCreds be used. Here using Respounder as an example:
After carrying out the hardening measures mentioned above and installing a honeypot, you may unfortunately find that there are attackers on your network.
Here it is possible to use the honeypot to collect information about the attacker and to check whether the GPO has actually been adopted by all clients.
If it is known from which IP the attack is coming, the attacker's port / MAC address can be blocked after sufficient information has been obtained in order to prevent further activities.
Especially in an emergency, we advise you to seek professional help and to document as much as possible.
ISO 27001:
A. 9.1.2 Access to Networks and Network Services
A.13.1.2 Security of Network Services
BSI Baseline Protection:
NET.1.1.A7
There is an entry in the MITER ATT&CK framework for the vulnerability:
PSN ID: PS-TN-2020-0006
