
The protection of privacy and one's own data is becoming more and more important with increasing digitization.
From For this reason, it is becoming increasingly important for end users to deal with the security of their data and privacy.
The article on the topic "Protect private data" is intended to give a brief insight into current methods of tracking on the Internet and to propose various measures to ensure security, privacy and Privacy of the end user on the Internet.
In order to understand how to be able to better protect your own private data, it is helpful to know the different methods of tracking of individual providers.
In order to protect your private data, you should also deal with tracking pixels in addition to cookies. In contrast to cookies, a 1×1 pixel is built into the page for tracking pixels, which is loaded from another server. This pixel is not visible to the visitor, but ensures that a corresponding call is made to the web server from which the pixel is loaded. In this way, the operator of the web server receives information about the IP address from which the page was accessed.
In this way, it can also be checked whether an advertising email has been opened, since in these cases the web server is called up. These methods can also be used by spammers or by phishing attacks used to be able to recognize whether spam mails have been opened by the recipient and thus determine that it is a valid e-mail address. Many mail clients now prevent the reloading of further web content. However, this may not apply to direct calls from the browser.
In order to be able to protect your private data, you should determine how you can be tracked yourself. Each time a page is called up via the Internet, information about the visitor is transmitted to the server. This concerns, among other things, the browser used, the screen resolution, installed plug-ins, the color depth, the installed fonts, language and time zone settings and the operating system used with patch status. The operator of a site can now try to use this information to distinguish between individual users. Practice shows that such a distinction is error-prone, but possible in principle. How easily you can be tracked by device fingerprinting can be seen e.g. B. can be determined on the following page: panopticlick.eff.org/

Many application providers now offer configuration options to increase the security of their own data and to give the user a higher level of privacy.
Weak passwords are a common reason for user account takeovers. Irrespective of the application, 2-factor authentication should therefore be used as far as possible. In addition, you should make sure that you use a separate password for each service - a Password manager give good support.
In order to protect your private data, you should also regularly check where you use social logins. As a rule, every provider such as Facebook, Instagram and Google offers such an overview.
In the Google account, many settings can be configured to improve privacy protection in the data and personalization area. For example, you can set here to what extent your search history is stored on YouTube and when it should be deleted.
If you use Google Maps, your geodata may also be stored by Google. You can also view and deactivate this in your Google account.
Google also stores data for other services relating to your Google account - for these services too, you can choose - in order to protect your private data - whether and after what time interval they should be deleted again.
Every user has the option of simply checking their own settings quickly in their Facebook account and identifying opportunities for improvement. These can be found in your own profile in the "Settings and privacy" area under "Privacy check".
In the "Who can see what you post" section, you should check whether the settings correspond to your own wishes in order to protect private data.
Under the "How others can find you on Facebook" section, there is also the option of configuring the account in such a way that your own Facebook account is no longer found via Google search.
Some settings can also be made on Instagram. So it is possible to decide in the privacy settings whether other users can see when you were last active on Instagram or whether other people can share your own messages.
With WhatsApp, a 2-factor authentication can be activated in the settings in the security area in case this account is set up on another device.
There is also the option under the "Data protection WhatsApp" tab to provide the app with additional authentication, e.g. B. FaceID to provide. This can prevent other people who are given the phone from accessing your messages. In addition, in the data protection area, it can be specified which persons are to be shown information about WhatsApp at all.
None of this helps against the fact that WhatsApp as a company itself has the ability to understand metadata about the communication, i.e. which people regularly communicate with each other. Since 2018, the company has also shared some of its data with the parent company Facebook.
Data protection-friendly messenger alternatives are Signal or Threema, but often you have to convince your own circle of acquaintances to do so.
In some areas, the GDPR has resulted in users being given more choice over how vendors handle their own data. Unfortunately, this also means that users are confronted with a wide range of setting options in cookie banners when they visit pages. Providers try to "steer" the user to allow as much tracking as possible through color design or intuitive click paths. In today's discussion, this is now known under the catchphrase "dark patterns".
Browser extensions that automatically block tracking tools on pages - regardless of what is selected in the banner - can help. There are now also extensions that automatically select the least invasive setting directly in the cookie banners of the common providers and confirm this. This can result in an enormous gain in convenience and better protection of privacy. Well-known examples of such extensions are Ghostery, uBlock or the Cookie Popup Blocker.
Also worth mentioning at this point is the browser Cliqz, which is based on FireFox and convinces with privacy-by-default. However, the project was discontinued in May 2020.
In the meantime, the common browser manufacturers are also showing developments in the direction of privacy-by-design and default directly on the browser side. The new version of Apple's Safari browser already has tracking protection integrated.
The TOR network is a well-known way of surfing the Internet anonymously. This is primarily used by data protection officers, politically persecuted people, but also criminals to surf the Internet undetected. The TOR network is also the "door" to the dark web, since many pages on the dark web can only be reached via the TOR browser or similar networks, so-called onion networks.
The TOR network consists of a meshed network of so-called onion routers. The onion routers themselves know the other onion routers in the network. Each router only saves its predecessor and successor for each connection for this connection in order to enable communication, and forms a so-called circuit.
If the end user establishes a connection to a service, the connection is routed through the TOR network and a connection is established. To do this, he must use a proxy himself, which serves as an entry point into the TOR network. Every connection through the TOR network passes through an entry node, through a relay node, to an exit node. After the exit node, the connection is routed through the Internet via the normal route.
As the data is routed through the TOR network, it is encrypted with the individual keys of the nodes. A node can only see from whom it received a packet and determine the next recipient of this packet. This also ensures that the operator cannot draw any conclusions about the participants in a communication if a single node is compromised.
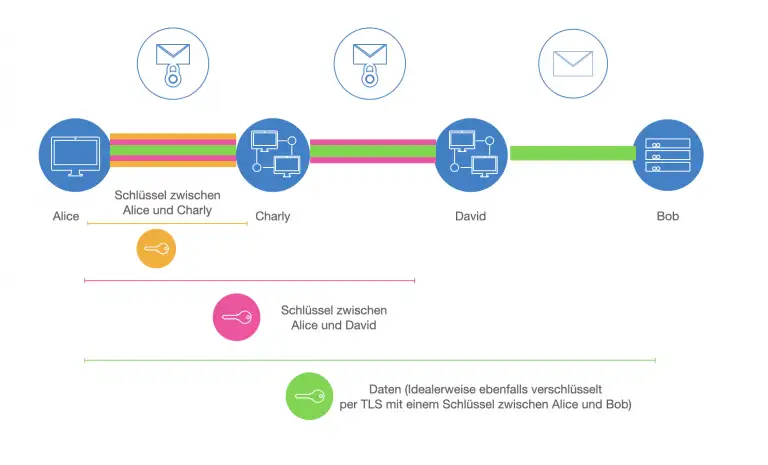
The figure shows a connection from Alice and Bob via Charly and David as well as the individual "shells" with the different keys that are used in the course of communication. It is a simplified representation to illustrate the principle of nested ciphers.
Performance problems can occur when using TOR, since the packet size is fixed at 509 bytes of user data (a "normal" TCP/IP or TLS packet usually has up to 1400 bytes available for data transport) and each additional packet still has to be routed through the onion network to the "normal" route.
While the TOR network offers basic traceability protection, there are two key points to keep in mind to protect your private data.
On the one hand, anonymity can only be guaranteed if the user is not logged on to Facebook or Google via the TOR network at the same time. If they do, it is of course still possible for the respective operators to identify the user.
The user should also be aware that the security of the connection can only be guaranteed if the service itself also offers encryption of the connection via TLS. Otherwise, the data can be read in plain text by anyone at the latest from the starting point of the TOR network - including the operators of the corresponding exit nodes.
As already indicated in the previous section, the operator of exit nodes can in principle view the data traffic of end users if they communicate with an unencrypted page (no TLS). Since the beginning of 2020, a group has been trying to exploit this fact by trying to gain control of the majority of the network's exit nodes. In the meantime, the group is said to have controlled over 1/4 of the worldwide exit nodes. (Source: https://www.zdnet.com/ article/ a-mysterious-group-has-hijacked-tor-exit-nodes-to-perform-ssl-stripping-attacks/)
In combination with other attacks, such as SSL stripping, the attackers are thus able to read the traffic from the users of the TOR network. For example, attempts were made to steal passwords for bitcoin accounts.
A “side project” by security researcher Edin Jusupovic from 2019 shows how easy it is to control many exit nodes (https://twitter.com/oasace/ status/1135473233925296129).
The scenario becomes even more dangerous if the group controls not only exit but also entry nodes. In these cases, purely by analyzing the incoming and outgoing traffic, it can be determined which parties are communicating with each other. For this purpose, the frequency of the incoming packets and their sizes are compared. Knowledge of the meta data is sufficient.
A list of current TOR exit nodes can be viewed at any time on the TOR project page.
As the previous illustrations show, the use of the TOR browser can also help private users to move undetected on the Internet and limit the possibilities of surveillance by companies. However, the user cannot completely avoid this if he needs to log in for individual pages.
The user should take particular care to ensure that the pages are always TLS encrypted despite the use of TOR, otherwise attackers in particular have the opportunity to read data traffic at the exit nodes in a targeted manner.
There are many ways for users to improve the protection of their own data and privacy on the Internet and some of them require little time. The use of TOR can be a suitable measure to protect privacy, but it is no guarantee that you will be completely anonymous on the Internet.
