

In a pentest, we assess broadly. This includes both technical aspects and physical security, as well as the human factor (social engineering).
So that we can comprehensively assess all areas in a short amount of time, we need information from you that real attackers would have to obtain themselves (e.g., information about the target network and its components).
During Red Teaming, we simulate a real attack as realistically as possible, defining a specific target (objective). We have more time for this process, allowing us to conduct information gathering without your support.
The Red Team is allowed to use any means to achieve the objective that malicious attackers would use. This includes, as in penetration testing, physical access and the human factor (social engineering). If one approach leads to success, no additional methods are tested.
Red Teaming assesses the responsiveness of your designated personnel and processes in a real incident scenario: What happens when IT happens?
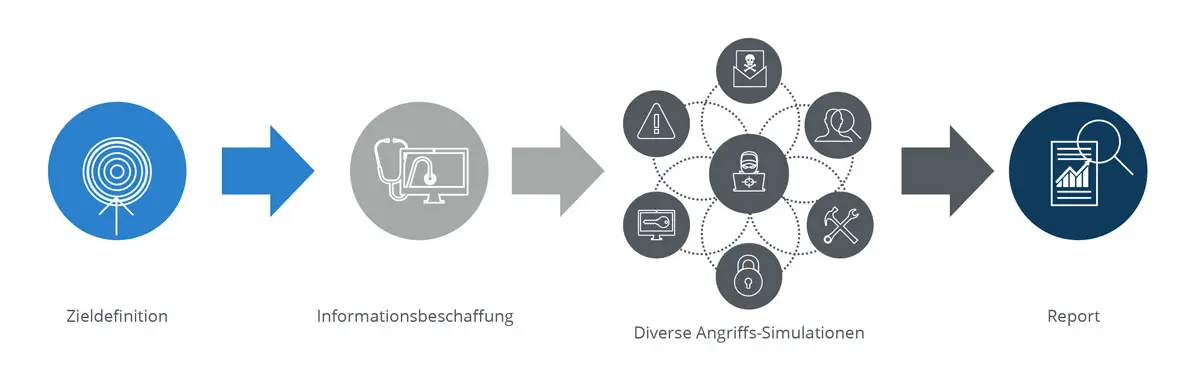
A Red Teaming attack scenario always focuses on an "Objective" that the Red Team aims to achieve. For this, the Red Team employs attacks via email, physical access, or other technical means.
Your company deploys its Blue Team against our Red Team, which is responsible for detecting and ideally thwarting our attacks. Therefore, your company's IT team should have the necessary resources and capabilities to focus on security issues and drive them forward. Ideally, your company should have individuals dedicated exclusively to IT security, including roles such as the Blue Team, Security Operations Center (SOC), Computer Emergency Response Team (CERT), Vulnerability Management, and a Security Department.
Does your IT security mechanism withstand every penetration test. And, how do they perform against attacks that are planned and executed over an extended period?

... subject the entire IT security infrastructure to a realistic stress test over a longer period of time.
This is the only way your company can get an idea of how the network and the SOC will behave in the event of a real attack. Based on this, we can solve any vulnerabilities found with you and your IT security department so that such attacks no longer work in the future or at least trigger an alarm for you.
A large German jewelry manufacturer wanted us to audit the physical security of its main facility. Despite chip card readers at all entrances, we managed to enter one of the buildings through the official side entrance.
There, a storage room with a printer aroused our interest. First we checked whether this printer was in the domain, which IP address spaces were used and whether access data to other systems could be found in this way. We then found that there was another door in the storage room that gave access to a separate area without a key or chip card.
There were four 19 inch racks with the fire protection alarm system, server, patch panel and switches. We connected the laptop we had brought with us to a port on the switch using a LAN cable and received a DHCP lease. Through quick scans and man-in-the-middle attacks, we made ourselves the local administrator on a few Windows machines, with more to follow. Finally, we found the clear text password for a domain administrator on a server and had achieved our goal.
With one customer, we had agreed on the goal of compromising an administrator's client. But our first attempts didn't lead us any further: Externally, only a website without functionalities and the mail server could be found. Physically we could not gain access to the company. Even after dozens of attempts, spear phishing was unsuccessful: Thanks to sophisticated scenarios, the administrators actually considered our phishing emails to be valid and clicked on many of the links they contained, but the files downloaded in this way were never executed.
Finally, a Twitter post from the company gave us information that we could use: This post introduced a new employee who has been an expert on a specific endpoint protection for over 25 years. We then got hold of this same endpoint protection and developed a file that was not recognized by it. After three more phishing attempts using this file, we finally achieved our goal.
The municipal utilities of a location agreed with us on the goal of compromising their operational technology network (OT network) and maintaining access to the network. While we did not find any physical entry points during a night-time drone flight over the buildings, the company's paper containers were freely accessible on the premises.
Through dumpster diving (searching for useful information in garbage) we came into possession of a delivery note from an IT service provider. That matched our research, according to which the IT of the public utility company was mainly implemented by external service providers.
In the next step, we used this information for vishing (voice phishing, fraudulent phishing phone call): We pretended to be the person responsible for the IT service provider we found and were thus able to find out where the control and control units for the OT were . It turned out that the entire OT was located on a separate air-gap network - so access from the Internet was not possible. That's why we smuggled an intern into the company – quite regularly via applications. During the management of the company on the first day of the internship, we were given access to sensitive areas of OT. We were able to place network sniffers with an LTE connection there – labeling them with the label “Please leave IT where it is”. This is how we managed to compromise the OT network despite the air gap.

Every company has individual requirements and conditions when it comes to Red Teaming.
We do justice to this by defining tailor-made objectives and framework conditions in coordination with your company in a threat modeling workshop.
In Red Teaming, we use two of our greatest strengths: Social engineering and experience testing physical access to your business.
The best security components are of little use if attackers can easily penetrate your server room or if people with network access open manipulated email attachments.
Ahead of the Red Teaming exercise, we conduct a kickoff meeting to identify the participants and ascertain the information and documents needed from your organization. This could encompass network diagrams, architectural details, asset inventories, domain listings, personnel records, and site locations.
The Threat Modeling Workshop takes place at the beginning of the Red Teaming process and is intended to establish the parameters for our engagement. At this stage, we need the documentation mentioned during the kickoff meeting from your organization. The critical aspect of the workshop is to conduct threat modeling for all potential approaches by the Red Team, enabling the team to act realistically while strictly adhering to discussed boundaries.
The following questions will be answered in detail during the threat modeling workshop:
The form of Red Teaming refers, among other things, to the level at which our Red Team should ideally attack your Blue Team. We adapt to the level of experience and skills of your IT department. There is also the question of whether the red teaming should be carried out covertly or openly and whether the red team and blue team should work together or act completely independently of each other during the mission.
Threat modeling (modeling of threats) is carried out to define the objective. Among other things, we use the MITER (ATT&CK) framework. In the Threat Modeling High Level Process we go through the following steps:
The red teaming is now carried out according to the results of the threat modeling workshop. There are fixed milestones/status dates that we have agreed on beforehand.
After completing the red teaming, you will receive the documented results and a summary from us as preparation for the subsequent workshop.
In a subsequent workshop, your Blue Team has the opportunity to engage with our Red Team to discuss the attacks and responses during our operation. The main focus here is on learning: our Red Team can, for example, demonstrate their attacks/kill chains to your Blue Team and show how they can be thwarted. This way, your Blue Team can better understand potential attackers and implement appropriate defense measures in the future.
Your company is already well positioned in the field of IT security. Experience in penetration testing is available. Your dedicated IT security team (SOC, CERT or comparable) has already established security mechanisms and is looking for a real challenge in the verification. Then the basic requirements are met.
While a penetration test takes about 6-10 days and lasts a maximum of 1-2 months, red teaming involves significantly more effort, which, depending on the objective or security level, can take 2- 6 months results.
At ProSec, the following people are responsible for the successful implementation of Red Teaming at your company:
This depends on the specific objective and the coordinated approach, which we agree on together in the scoping workshop. Normally, however, regulated communication takes place during the implementation. You will receive the processed overall result at the end.
This depends on the specific objective and the coordinated approach, which we agree on together in the threat modeling workshop. In most cases, however, a regulated exchange between defined key persons is necessary or useful. If necessary, we also use a "Purple Team(ers)".
This depends on the specific objective and the coordinated approach, which we agree on together in the threat modeling workshop. Experience has shown that we most often succeed in “initial access” via human or physical access.
This is an agenda item for the Threat Modeling Workshop.
This is an agenda item for the Threat Modeling Workshop.