| WORD | EXPLANATION |
|---|---|
| Vulnerability type | specifies which vulnerability type affects the finding. |
| Vulnerable version | describes the vision associated with the vulnerability. |
| Vulnerable component | names the susceptible devices of the vulnerability. |
| Report confidence | here you can find the detailed report of the vulnerability. |
| Fixed version | names the repository version. |
| Vendor notification | explains what the vendor responds about this vulnerability. |
| Solution date | specifies the resolution date of the vulnerability. |
| CVE reference | is an industry standard that aims to introduce a unified naming convention for vulnerabilities. |
| CWE | is a category system for software weaknesses and vulnerabilities. |
| CVSSv3 Calculator | shows the components of the Common Vulnerability Scoring System. |
| Researcher Credits | names the researcher who found the vulnerability |
| Vulnerability Details | describes the exact details of the vulnerabilities and which devices are affected. |
| Risk | describes the effects the vulnerability might have. |
| Steps to reproduce | explains the way to reconstruct the vulnerability. |
| Solution | shows a possible solution to fix the vulnerability |
| History | describes the history of the vulnerability, when it was identified, and how it progressed further. |
The company that concerns the security vulnerability must officially announce the researcher in
the „Advisory”. In addition, ProSec GmbH is allowed to name the company as a reference.
If a bug bounty program exists, the ProSec GmbH is entitled to claim the proceeds
If the company concerned does not react within 14 days to the announcement of the security
gap, then the full disclosure, including PoC codes, will be published.
If the company concerned reacts to the disclosure within 14 days, a coordinated disclosure is
carried out, if the vendor is affected, a joint fist is set to solve the problem.
After the vulnerability is fixed, we wait 14 days until the release (excluded from the disclosure are
the PoC codes). The publication gives customers the opportunity to fix the vulnerabilities
through updates provided by the vendor. Our goal in this strategy is not to create imitators. To
illustrate our process, you will find two timelines below:
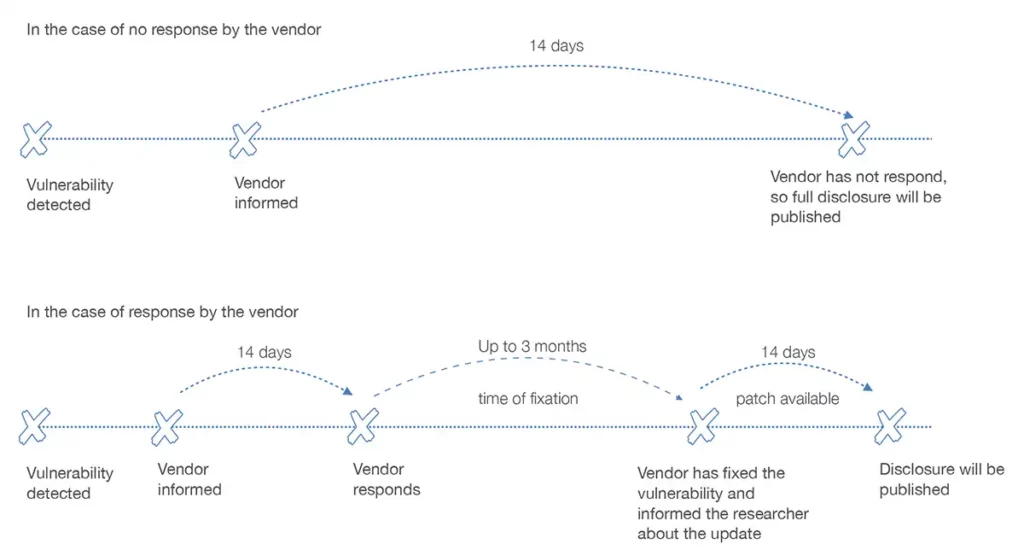
All parties involved must be aware of the deadlines and consequences of this disclosure.
Wir verwenden Cookies, und Google reCAPTCHA, das Google Fonts lädt und mit Google-Servern kommuniziert. Durch die weitere Nutzung unserer Website stimmen Sie der Verwendung von Cookies und unserer Datenschutzerklärung zu.