
The Common Weakness Enumeration, or CWE for short, is a system designed to categorize hardware and software weaknesses or vulnerabilities.
The community designed list has been operated by MITER Corporation since 2006.
It serves as a common language and basis for identifying security-critical vulnerabilities.
The list includes, among others Vulnerability Analysis or penetration testing for use. Furthermore, this list helps to contain and delimit, as well as to prevent possible weaknesses in software and hardware. Members of the CWE community include big names such as Apple, Oracle and Microsoft. The project is funded by the US Department of Homeland Security (DHS) and the Cybersecurity Infrastructure Security Agency (CISA).
The main goal of the CWE is to prevent CVEs (Common Vulnerabilities and Exposures) whenever possible. In order to achieve this, a CWE not only contains a detailed description of vulnerabilities, but also provides examples and solution approaches for eliminating these vulnerabilities. The list can be equally helpful for security researchers and programmers and can offer practical benefits for the respective application.

Due to the detailed description of the vulnerabilities, it is also possible to use them for similar problems in other programs.
In addition, the CWE list is also used in various vulnerability scanners or when creating new programs. Programmers can use the CWE list to find out about known vulnerabilities and errors in other programs and take this information into account when developing a new program.
A CWE ID is formed like a CVE as follows: CWE-XXX.
This is a unique ID. The CWE list in version 4.1 currently includes over 800 vulnerabilities divided into over 300 categories.
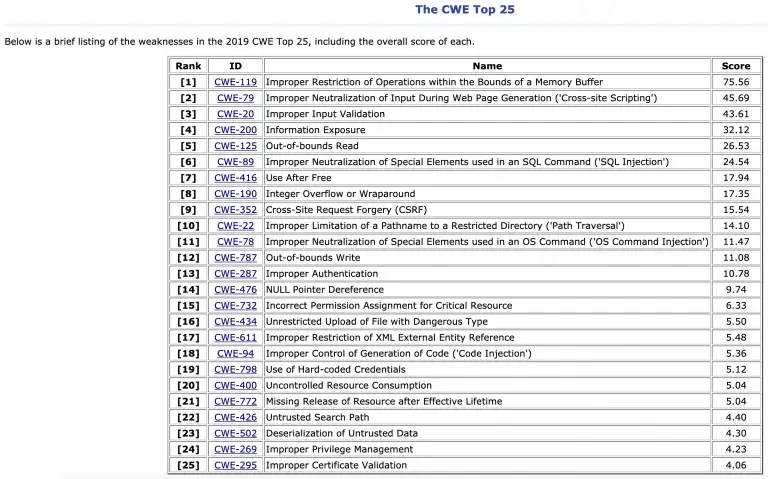
Similar to the "Open Web Application Security Project", OWASP for short, there is also a list of the "Top 25 Most Dangerous Software Errors", the so-called "CWE
Source: cwe.mitre.org
Top 25”, in which, for example, the “CWE-2019 Use of Hard-coded Credentials” was in 798th place in 19. Other well-known classes include buffer overflow, cross-site scripting, SQL injection and OS command injections.
Application of the CWE at ProSec GmbH
At ProSec GmbH, CWE and CVE are used in the area of pentesting and IT security consulting - mainly in the context of documentation, classification of vulnerabilities and as a basis for uniform "wording".
We use cookies, and Google reCAPTCHA, which loads Google Fonts and communicates with Google servers. By continuing to use our website, you agree to the use of cookies and our privacy policy.
