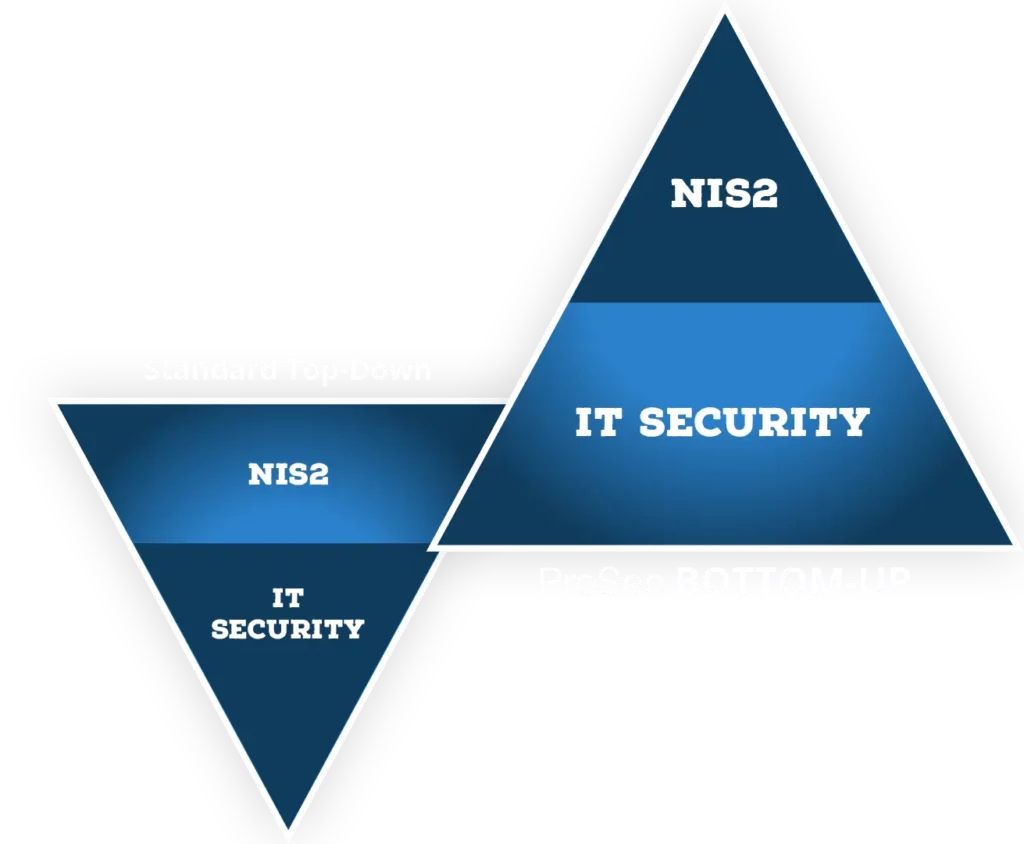
The ProSec approach to the NIS 2 Directive:
Bottom-Up for Sustainable Information Security
For many companies, the European NIS 2 directive and its national implementation feel like a difficult upcoming exam in which the modalities have not yet been determined: the tasks are extensive, time is short and failure may result in severe penalties. Given this potential Threat, it's easy to lose sight of what all of this is essentially about: better protection for companies and the public from the very real threat posed by criminal hackers.
Therefore, our Bottom-Up approach initially focuses on what is already established and functioning well in terms of IT security within your company. We use this status quo as a foundation to work together on optimizing your information security. With this foundation, you can quickly and successfully respond to the actual requirements in the German implementation of NIS 2.
This way, you implement the NIS 2 Directive in your company as it was intended: as a catalyst for greater cyber resilience that will strengthen your organization in the long term.





