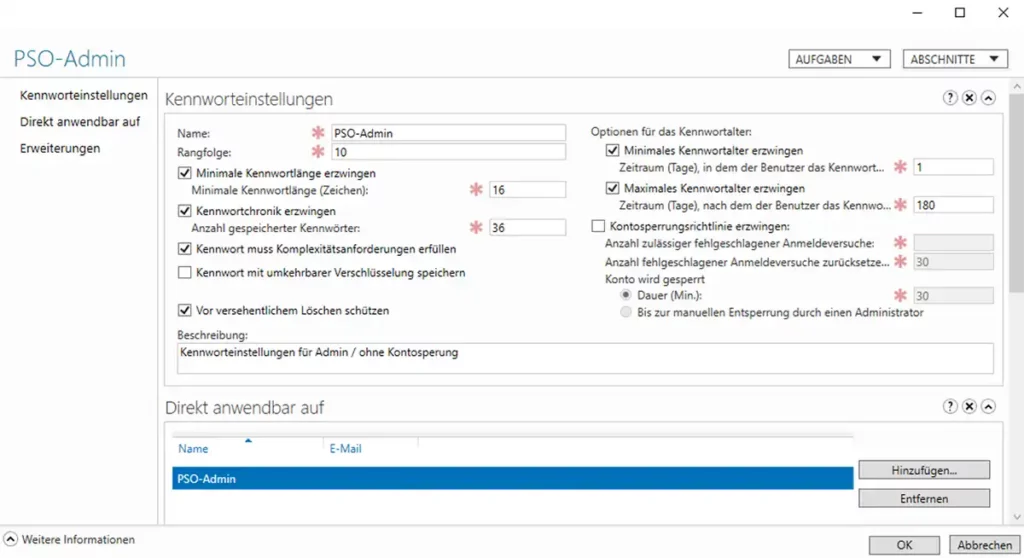
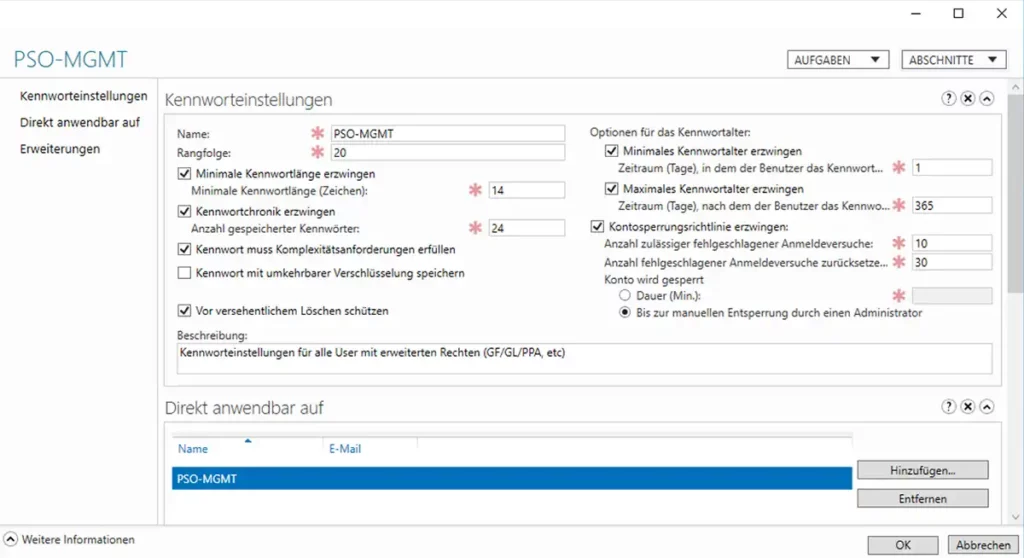
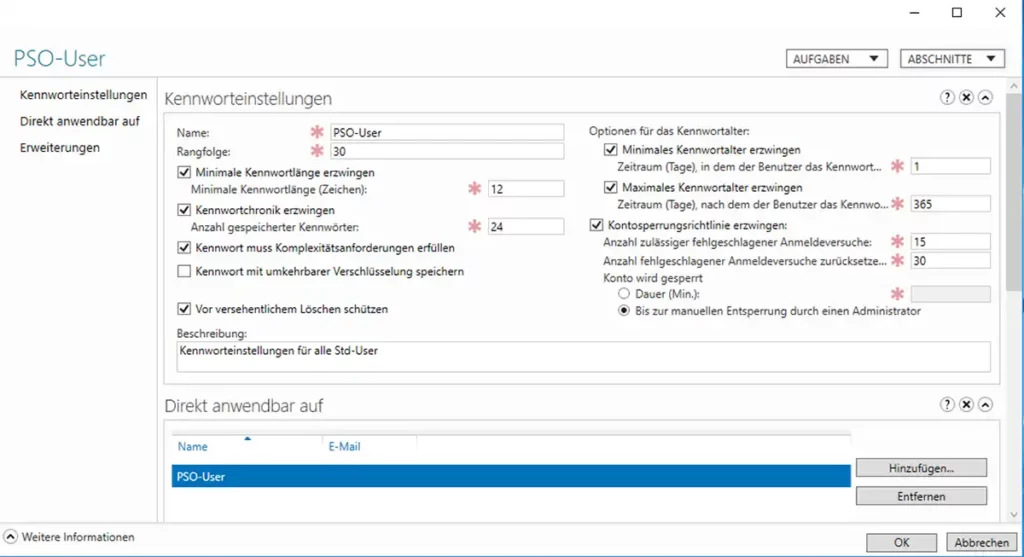
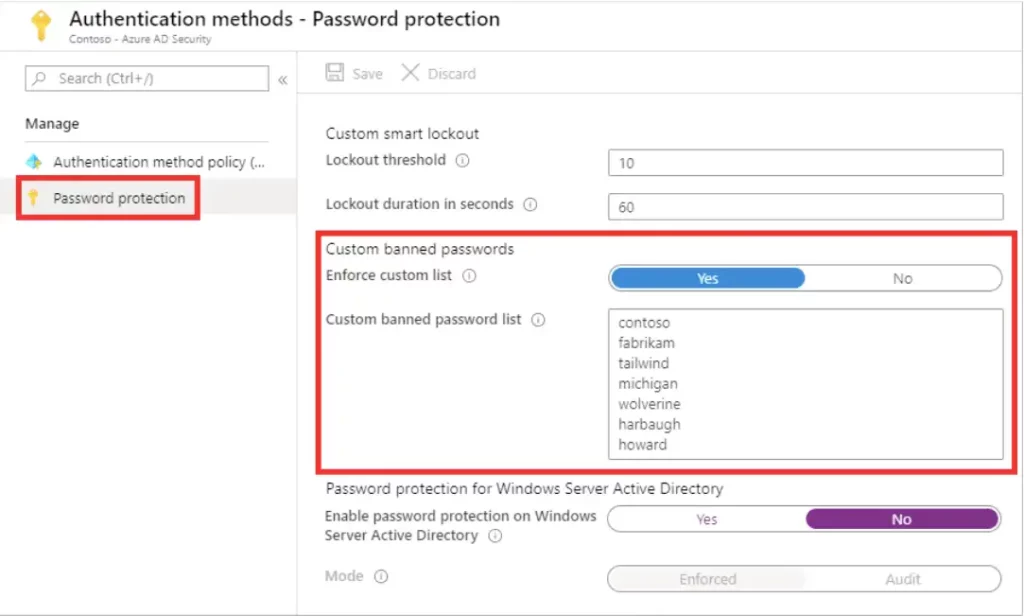
The cyberattack on the crypto exchange Coinbase has shown that insiders can pose the greatest threat to companies. It's not just technical vulnerabilities, but especially human vulnerabilities that enable cybercrime. This article explains why insider threats pose a particular risk and what measures companies can take.