
The protocol was originally called the Secure Sockets Layer. With the introduction of TLS 1.0, the term Transport Layer Security was introduced. The terms TLS and SSL are often used interchangeably in practice. However, protocol versions SSL 1.0-3.0 and TLS 1.0 and 1.1 are outdated and insecure and should no longer be used. The current version of the protocol is TLS 1.3.
TLS connects asymmetric and symmetric encryption methods (hybrid encryption protocol) to enable two parties to communicate encrypted over a network. If content is not encrypted during transfer, there is a possibility that other participants (e.g. network operators or other parties with access to the data traffic) may read or change this content.
In order for communication to be considered secure, at least one of the communication partners must confirm their identity using an asymmetric cryptographic process. When communicating on the Internet, this is usually the server. So-called public key certificates are usually used for this purpose. These confirm the identity and properties of a public key of the certificate holder, provided the certificate is issued and certified by a trustworthy certification authority. In most cases, the crypto system is used for this step RSA employed.
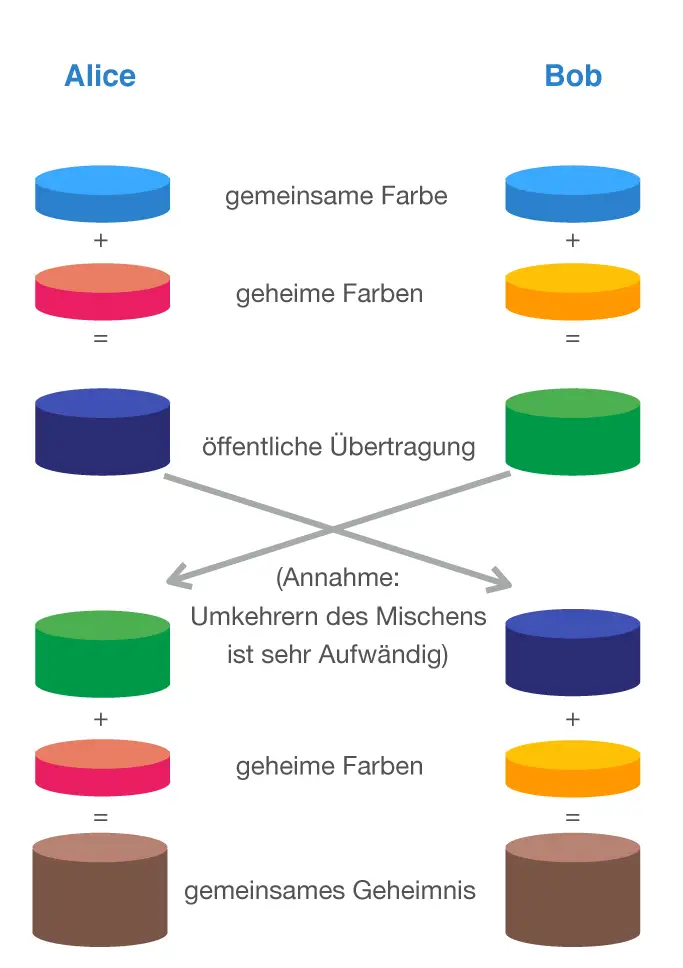
After authentication has taken place by checking the certificate, an asymmetric cryptographic process is used again, through which the partners agree on a shared, secret key, which can then be used to further encrypt the data traffic. This is usually what happens here Diffie-Hellman protocol for use. The Diffie-Hellman key exchange allows communication participants to calculate a common key from this data by exchanging unencrypted data. Both partners have a different private part as the basis for exchanging keys. This private information will not be transmitted and must remain strictly confidential. A potential attacker cannot use the public information used to agree on the secret shared key to calculate or guess the shared secret key in a realistic time.
The Diffie-Hellman protocol is particularly useful when used to encrypt content on the Internet using the Https standard, because the usual communication partners in this context, a web server and a client (or its Internet browser), generally do not have any information about each other and therefore cannot have a common key in advance with which they could encrypt content symmetrically.
Once a shared secret key has been agreed upon, it can be used to encrypt the actual content of the communication in order to then transmit it. A symmetrical encryption method can be used for this. With these methods, content is both encrypted and decrypted with one key, the encryption is therefore reversible and therefore symmetrical. The currently most popular symmetric cryptosystem is the Advanced Encryption Standard (AES) with this information can be encrypted with keys with a length of 128 bits (AES-128), 192 bits (AES-192) and 256 bits (AES-256). The longer the key used, the more secure the encryption is. This algorithm is also often used with TLS, but other encryption methods can also be used.
For TLS, there are various so-called cipher suites that standardize the use of certain encryption and authentication procedures. These suites specify which procedures are used for the following steps of the protocol:
Example Cipher Suite:
ECDHE–RSA–AES256-GCM–SHA384
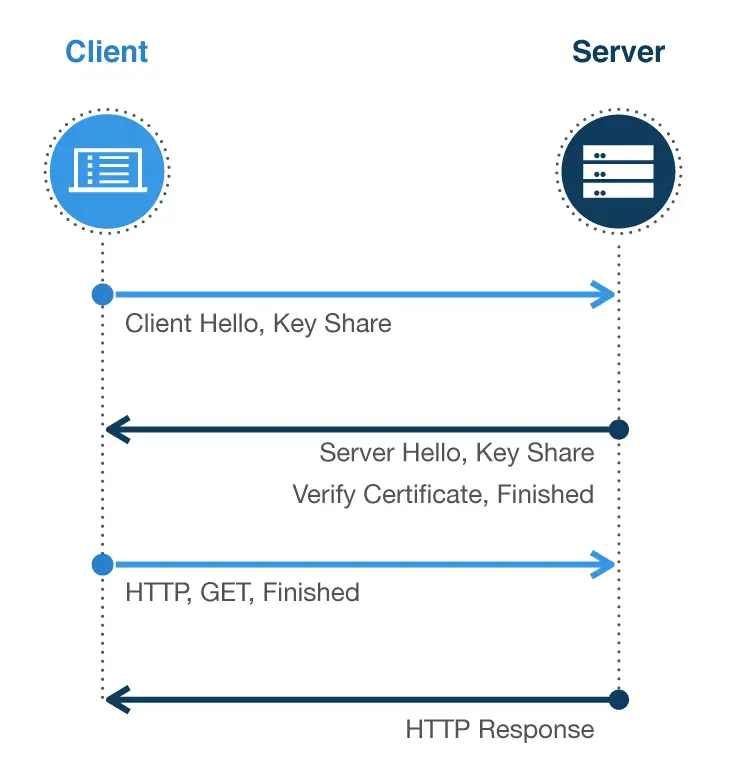
As part of the TLS handshake, the communication partners agree on a chiper suite, which is then used subsequently.
With the current standard of the TLS 1.3 protocol, part of the protocol has been firmly defined. This is necessary for key exchange Elliptic Curve Diffie-Hellmann Ephemeralprocedures can be used. This has the advantage that so-called “forward secrecy” is provided because the generated key is only valid for one session at a time. If a single key becomes known, it can only be used to decrypt the communication of a single session and not all of the data traffic exchanged up to that point. By specifying the key exchange procedure, the TLS handshake can run faster.
Another change with version 1.3 is a significant reduction in the number of permitted cipher suites. While there were 1.2 different suites in version 293, some of which are unsafe, in version 1.3 there are currently only 5 approved suites, all of which are currently considered safe. This greatly simplifies the selection of the suites used or accepted.
Example Cipher Suite: TLS 1.3:
TLS_AES_256_GCM_SHA384
TLS is used for encrypted transmission of various protocols. The best-known example is HTTPS, the encrypted version of the Hyper Text Transfer Protocol (HTTP). This is used, for example, for encrypted access to websites. When transmitting sensitive data, such as log-in forms, the use of TLS encryption is often mandatory. Modern browsers also warn against transferring such data from forms without encryption.
Further fields of application include the protocols POP3S, SMTPS or IMAPS for the transmission of emails or SIPS for encrypted transmission of VOIP communication. There are numerous other applications for TLS.
Over the last ten years, the use of TLS and SSL has increased significantly. A large proportion of websites on the World Wide Web are now secured via TLS/HTTPS. This has a positive effect on data protection and IT security for Internet users.
However, it should be noted that in most cases there is no end-to-end encryption because SRTP can only guarantee an encrypted connection from an end device to the service provider (e.g. the telephone provider). The user has no influence on whether the provider subsequently encrypts the data transmission to the recipient. At least the provider decrypts the data. The ability to decrypt data and therefore view and evaluate it is often desired.
In Germany, for example, the TKG (Telecommunications Act) provides for the possibility for law enforcement authorities to request and view unencrypted communication data. Telecommunications service providers are legally obliged to provide this opportunity to view communications.
We use cookies, and Google reCAPTCHA, which loads Google Fonts and communicates with Google servers. By continuing to use our website, you agree to the use of cookies and our privacy policy.
