
They are usually untargeted or widespread attacks by criminal hackers. For example, they send fake e-mails that look like those from Amazon, Telekom or DHL - if you open the links they contain, malware, a virus, is installed unknowingly and in the background.
One form of the virus is what is known as ransomware (a portmanteau of ransom, English for ransom and software). Hackers use this to block computer programs, data or folders directly - their goal: They demand a ransom from the victim to remove the blocking, otherwise the data will be deleted or even released on the Internet. Affected companies are therefore interrupted in their business operations, lose sales or face penalties and damage to their reputation, e.g. B. Sensitive customer data such as payment information, patient files or media such as photos and videos are made publicly available. The perfidious: Such ransomware is programmed to break through the virus protection and even backups (if they are made).
In order to mitigate the financial consequences of an attack, there are so-called cyber insurance policies, which essentially include the following services:
Cyber insurance is ideally part of a holistic cyber security concept, which also includes the following components and is offered by IT security companies.
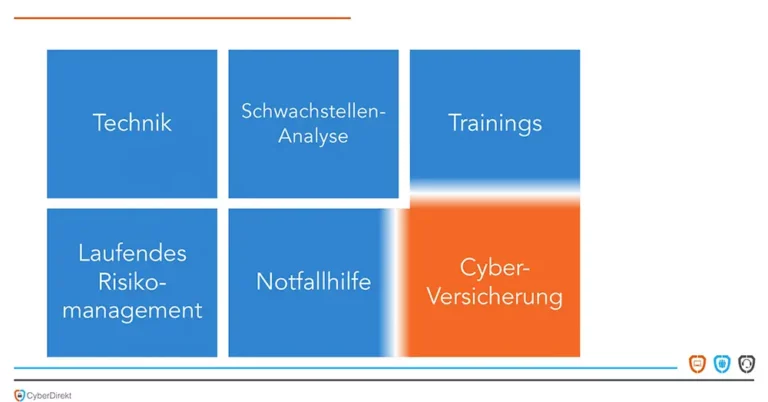
Emergency help is available 24/7, 365 days a year in case of emergency. IT forensics experts immediately analyze the extent of the cyber attack. They initiate immediate measures to minimize the damage and to avoid consequential damage. The experts then ensure that the systems and data and thus the "normal state" can be restored Crisis communication with z. B. Employees, customers and business partners support cyber security providers in order to prevent or minimize reputational damage and to overcome the crisis of the attack.
